April 29, 2006
Opinion by Ira Winkler
To manage risk, you must first define it. While there are many risk formulas, the one that I have found to be most effective is the following quasi-mathematical construction:
Risk = ((Threat * Vulnerability) / Countermeasure) * Value In this equation, value is the amount that your information and/or services are worth. Notice that I did not refer to the value of your IT, such as the hardware, software and support personnel. The fact is that hardware and software are fungible, and the cost of its replacement is trivial when compared to the value of the data on a computer. A backup tape, for example, might be costly, but it's worth millions if it's storing credit card numbers -- when you consider the potential financial fraud, the cost of reissuing the cards and the loss of business resulting from the loss of customer confidence.
Source:
http://www.computerworld.com/
Opinion by Larry Ponemon
APRIL 25, 2006 (COMPUTERWORLD) - Perhaps you were chosen for additional airport screening while rushing to catch a flight. Or you noticed a video camera watching your every move the last time you entered a bank, shopping mall or department store. Responses vary when people are confronted with actions aimed at improving security or service, which may also affect their privacy. We recently conducted a survey seeking opinions about several different surveillance methods:
Source:
http://www.computerworld.com/
A look at what's on tap for the next version of Internet Explorer
APRIL 24, 2006 (COMPUTERWORLD) - The biggest visible change in Internet Explorer 7 may be the addition of tabbed browsing, but an even more important improvement lurks under the hood: Microsoft has added a host of substantial new security features, including
antiphishing tools, malware protection tools, automated security protection and more. A look at the just-released Beta 2 of IE7 reveals a number of changes and adaptations.
Source:
http://www.computerworld.com/
What Matters In Up-To-Date Data Centers
With hackers and malware, spam and zombies (servers that “sleep” until daemons instruct them to launch a DoS attack), today’s IT experts have more threats to deal with than ever. Don Purner knows the issue well. As CTO and vice president of Dataside, he oversees five enterprise-class data centers where small and midsized enterprises colocate their systems. It gives him a keen view of their security concerns
Source:
http://www.processor.com/
Thursday, April 20 2006
ImageWare's development of biometrically-enabled identity management solutions using an extensive open architecture approach has earned it a Frost & Sullivan Product Innovation of the Year award in the biometrics market.
Source:
http://www.secureidnews.com/
News Story by Jaikumar Vijayan
APRIL 21, 2006 (COMPUTERWORLD) - Westchester County, N.Y., this week enacted a new law that requires local businesses to implement “minimum security measures” for protecting their wireless networks.
The law, which is believed to be the first of its kind anywhere in the country, applies to all commercial businesses that collect customer information, such as Social Security numbers, credit card or bank account information, and that also have a wireless network. Also covered by the law are businesses that offer public Internet access.
Source:
http://www.computerworld.com/
The buggy first version caused headaches for some users
News Story by Robert McMillan
APRIL 21, 2006 (IDG NEWS SERVICE) - Microsoft Corp. plans to reissue a security patch for its Windows operating system that caused serious headaches for some users.
The MS06-015 security update was released last week, but Microsoft customers soon reported that it was causing applications to crash thanks to a conflict between the patch and NVidia Corp.'s video drivers and Hewlett-Packard Co.'s Share-to-Web photo-sharing software.
Source:
http://www.computerworld.com/
The rule of least privilege and separation of duties will keep users out of network places they don't belong. Security Manager's Journal by Mathias Thurman
APRIL 24, 2006 (COMPUTERWORLD) - As information security professionals, we tend to throw around certain terms when we talk about how information security should be implemented. Lately, when I've gone to meetings or written an e-mail that gives me a chance to evangelize about our security needs, my terms of preference have been "rule of least privilege" and "separation of duties."
Source:
http://www.computerworld.com/
Proof-of-concept exploit utilizes OS X, Safari holes
News Story by Robert McMillan
APRIL 21, 2006 (IDG NEWS SERVICE) - A Mission Viejo, Calif., security researcher has posted code that exploits a number of newly discovered and unpatched bugs in the Mac OS X platform.
The software, posted Friday by independent researcher Tom Ferris, could be used to crash applications or even run unauthorized code on the Mac by taking advantage of bugs in the Safari browser and Mac OS X operating system. Ferris's "proof of concept" code exploits a total of seven bugs.
Source:
http://www.computerworld.com/
Opinion by Douglas Schweitzer
APRIL 24, 2006 (COMPUTERWORLD) - So, you just set up a shiny new wireless router at home or at your office. As convenient as it is to have no strings, or at least wires, attached, that new router may have punched a hole in your security schema and set you up for unwanted trouble.
The reason you could now be vulnerable is simple: default settings. Remember, manufacturers often turn off security and certain other features by default so that their products will be easier to set up and integrate into a wide variety of networks. Source:
http://www.computerworld.com/
April 28, 2006
The counterpart to needing trustworthy channels is assuring users that they really are working with the program or system they intended to use.
The traditional example is a ``fake login'' program. If a program is written to look like the login screen of a system, then it can be left running. When users try to log in, the fake login program can then capture user passwords for later use.
A solution to this problem is a ``trusted path.'' A trusted path is simply some mechanism that provides confidence that the user is communicating with what the user intended to communicate with, ensuring that attackers can't intercept or modify whatever information is being communicated.
Source:
http://www.dwheeler.com/
April 26, 2006
Group also hopes to "make Bill Gates soooooooooo mad"News Story by Elizabeth Montalbano
APRIL 25, 2006 (IDG NEWS SERVICE) - A group of self-described "political activists" in Massachusetts has started an aggressive campaign to get browser users to switch from Microsoft Corp.'s Internet Explorer to Mozilla Corp.'s Firefox.
The campaign, called Explorer Destroyer, takes advantage of a new program by Google Inc. to pay users $1 for each referral to Firefox made through Google Toolbar, according to the group's Web site.
"You already want people to switch to Firefox. Now's the time to get serious about it," according to the site. "Google is paying $1 for each new Firefox user you refer. ... Now you can advance your ideals, save people from popups and spyware hell, and make some serious money."
Source:
http://www.computerworld.com/
April 22, 2006
By John E. Dunn, Techworld
Scientists have reported an important speed breakthrough which brings closer the day when quantum encryption becomes a usable part of communications security.
The National Institute of Standards and Technology (NIST), a US government agency, has reported that it has managed to shift quantum-encrypted information at a “raw” throughput of 4 million bits per second across a 1 km-long fiber link.
This is at least twice NIST’s previous record, which has been rising since the agency announced it had broken the 1 million bits per second barrier in May 2004.
Source:
http://www.techworld.com/
What will IBM's new hardware-based security technology be used for?
By Kate Greene
IBM recently announced an effort to enmesh data security in the chips found in cell phones, PDAs, and other portable devices. More than half of all unprotected data can be found on these gadgets, says the company, and encryption that relies on software is not as secure as encryption built into hardware.
Source:
http://www.technologyreview.com/
April 21, 2006
News Story by Grant Gross
APRIL 19, 2006 (IDG NEWS SERVICE) - A media rights group has identified a third dissident who the
Chinese government arrested based on information apparently supplied by a Yahoo Inc. subsidiary.
The verdict document says Jiang's e-mail account, provided to Chinese authorities by Yahoo Holdings (Hong Kong) Ltd., was part of the evidence used to try him for the crime of subversion.
Source:
http://www.computerworld.com/
By C. J. Kelly
I read this opinion article by Mark Hall with interest. The title No Silver Bullet caught my eye. The article states "
We are years away from having a single security architecture to protect company information."
Mark talked to Nick Caffarra, president of Evalubase, a research organization, "
maybe, in five or more years there could be an integrated cross-technology security approach from one vendor capable of protecting your information."
We should not expect one vendor to address the gamut of security issues that need to be addressed. I would be suspicious of any vendor who said they could. Security touches every aspect of technology.
Source:
http://www.computerworld.com/
By Ryan Naraine
Microsoft has 'fessed up to hiding details on software vulnerabilities that are discovered internally, insisting that full disclosure of every security-related product change only serves to aid attackers.
The company's admission follows criticisms from a security researcher that its policy of silently fixing software flaws is "misleading" and not in the spirit of Microsoft's push for transparency.
"
We want to make sure we don't give attackers any [additional] information that could be used against our customers. There is a balance between providing information to assess risk and giving out information that aids attackers," Reavey said.
Source:
http://www.eweek.com/
By Edmund X. DeJesus, Contributor
Microsoft has announced that it will be ending support -- including security updates -- for its Windows 98, Windows 98 Second Edition, and Windows Millennium Edition (Me) on July 11, 2006. However, analysts suggest that the change won't exactly send shockwaves through the security community.
"Microsoft is retiring support for these products because they are outdated and can expose customers to security risks," Microsoft said. "We recommend that customers who are still running Windows 98 or Windows Me upgrade to a newer, more secure Microsoft operating system, such as Windows XP, as soon as possible."
Source:
http://searchwindowssecurity.techtarget.com/
Brien Posey, Contributor
I have some friends who swear to me that the phrase "Internet Explorer Security" is a contradiction in terms. While I don't agree, I can see their point. There are countless security holes that have been documented in Internet Explorer, and don't even get me started on the damage that a browser hijacker can do. Even so, Microsoft claims to be learning from its past mistakes. Internet
Explorer 7 contains a plethora of new security features that should help make the new browser much more secure than its predecessors and hopefully make the lives of administrators easier.
Definite helpURL handling
Cross-site scripting attack protection
ActiveX opt-in
Not quite ready for prime timeWindows Defender
Phishing filter
Will be great, as soon as Vista is deployedProtected Mode
Source:
http://searchwindowssecurity.techtarget.com/
Vendors turn to OPSWAT to better their products
There are dozens of brands of anti-virus, anti-spyware, desktop firewall and VPN products, and Benny Czarny has made it his business to know them all inside and out.
Vendors such as Cisco, F5 Networks, Symantec and Juniper Networks license the OPSWAT code that checks for more than 400 versions of security software from more than 35 vendors. They embed the code, a software development kit (SDK), into their network-access control products.
This has made
OPSWAT (which informally stands for
Omni-Platform Security with Access Technologies), a security vendor to security vendors, supporting methods of network-access control ranging from Microsoft's Network Access Protection to Cisco's Network Admission Control.
Source:
http://www.networkworld.com/
By C. J. Kelly
Identity theft is the problem of the customer. Seriously. The customer is responsible for guarding his or her personal information while it resides in their possession: on a laptop or home computer, in a wallet, in a briefcase, in a PDA, etc.
...
Identity theft is also a problem for the bank because it leads to bank fraud. Someone charges thousands of dollars to your credit card or uses your ATM Visa/MC card to deduct same from your bank accounts.
...
Suffice it to say that biometric authentication has been touted as solving both problems: identity theft and bank fraud.
Source:
http://www.computerworld.com/
News Story by Robert McMillan
Windows Server Update Services 3.0 is slated for launch in 2007
WSUS is a free alternative to Microsoft's Systems Management Server (SMS) product that gives customers a way to control the deployment of Microsoft patches and security updates. It will be shown in public for the first time during an April 27 session at the systems management conference.
The new MMC-based interface will give customers an improved view of how their patch deployments are rolling out and will allow them to roll reports from a variety of different servers into one root server, Dadzie said.
Source:
http://www.computerworld.com/
April 19, 2006
Webcast: Selected RSA® Conference 2006 ...Bill Gates
Chairman of the Board and Chief Software Architect
Microsoft Corporation
...Scott McNealy (
Intersting presentation)
Chairman and Chief Executive Officer
Sun Microsystems, Inc.
...Panel Discussion
The Cryptographers Panel
"Write down your password your wallet is more secure than your computer."Whit DiffieVice president, Sun fellow, and Chief security Officer sun Microsystems
Source:
https://2006.rsaconference.com/
It's also launching MSN Postmaster Services for Internet service providers
News Story by Elizabeth Montalbano
Sender ID allows companies to attach information to an Internet domain that tells e-mail recipients what addresses are authorized to send mail from that domain, Spiezle said. This allows the system that receives the message to recognize if it is legitimate or being spoofed by another domain, he said.
Source:
http://www.computerworld.com/Related link:
http://news.com.com/
Fourteen patches, plus a utility that finds unchanged default login info
News Story by Robert McMillan
APRIL 18, 2006 (IDG NEWS SERVICE) - Oracle Corp. has published a collection of software patches that address security vulnerabilities in a range of the company's products, including its database and application server software. As part of this update, it also released a tool designed to ferret out commonly used default passwords that theoretically could be misused by hackers.
Source:
http://www.computerworld.com/
William Eazel 18 Apr 2006 10:27
The use of rootkits to conceal both malware and commercially viable Potentially Unwanted Programs (PUPs) is on the rise, new research warned today.
According to the latest report from McAfee's AVERT Labs, in the last three years alone the incident rate of stealth technology has increased by more than 600 percent. The study considers
malicious programs using stealth technology to be rootkits, distinct from commercial applications that use stealth technology.
Source:
http://www.scmagazine.com/
René Millman 18 Apr 2006 11:54
Nearly half of IT professionals believe their infrastructures are not completely protected against vulnerabilities, new research has found.
The study, conducted by Ipsos Research, found that 45 percent of over 600 senior IT personnel throughout Europe questioned felt that their IT infrastructure was "never 100 percent protected from software and network vulnerabilities."
Other findings revealed that over a quarter (27 percent) of those questioned said it takes 48 hours or more from the time a patch is issued to the IT infrastructure being fully protected from that vulnerability. One in five (19 percent) said it takes up to a week or more.
Source:
http://www.scmagazine.com/
René Millman 18 Apr 2006 12:26
An Australian spammer has become the first person to be successfully prosecuted under that country's anti-spam laws.
The Western Australia-based spammer, Wayne Mansfield, and his company Clarity1, were found to have illegally sent more than 56 million spam messages to email addresses around the world during the 12 months since the act was introduced in April 2004.
Source:
http://www.scmagazine.com/
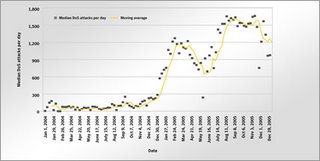
Over the last six months of 2005, Symantec detected an average of 1,402 Denial of Service (DoS) attacks per day. This is an increase of 51 percent from the first half of 2005, when Symantec detected an average of 927 DoS attacks per day.
Source:
http://www.symantec.com/
April 18, 2006
Tokyo, Japan, Apr 17, 2006 - (JCN Newswire) - Nippon Telegraph and Telephone Corporation (NTT) began to offer NTT's open source codes of the
128-bit block Cipher*1 algorithm "Camellia", jointly developed with Mitsubishi Electric Corporation (Mitsubishi) in 2000, using the C and Java languages on the Camellia home page, on April 13, 2006. This is based on the policy of expanding the international infrastructure technology to support a secure advanced information society as the first Japanese encryption algorithm.
Source:
http://www.japancorp.net/
By Chris Mellor, TechWorld, 04/12/06
Everdream has launched a service to delete or encrypt files on stolen PCs and laptops. But the service depends utterly on the thief being naive enough to connect the stolen PC/laptop to the Internet without wiping the existing software on the hard drive first.
Source:
http://www.networkworld.com/
April 17, 2006
IT leaders are taking a more businesslike approach to security and risk management.
Opinion by Mitch Betts
APRIL 17, 2006 (COMPUTERWORLD) -
We secure information systems because the business would be brought to its knees if we didn't protect trade secrets, vital corporate networks and sensitive data. Yet the business would also be brought to its knees if we spent every last dime in the treasury on security.
Yes, it's possible to overspend on security. The trick is to figure out how to reach what ex-CIO Doug Lewis calls "
the prudent zone" of security investment.
Source:
http://www.computerworld.com/
Bill not yet a law, but developers are already feeling the squeeze
News Analysis by Peter Sayer
APRIL 14, 2006 (IDG NEWS SERVICE) - On May 4, the French Senate will debate a copyright bill that is widely expected to have a chilling effect on the development and distribution of open-source software for digital rights management (DRM) or P2P (peer-to-peer) file-sharing. That's because the bill's provisions include a penalty of up to three years in prison and a fine of $363,171 for publishing, distributing or promoting software in France that is "manifestly intended" for the unauthorized distribution of copyright works.
The developers of the open-source multimedia player VLC, which can read DRM-protected DVDs, consider themselves targeted.
...
Open-source projects are thought to be more vulnerable than commercial operations because they typically have few resources at their disposal to defend legal actions.
Source:
http://www.computerworld.com/
News Story by Robert McMillan
APRIL 14, 2006 (IDG NEWS SERVICE) - Significant changes made in a security patch from Microsoft Corp. to the way Internet Explorer processes ActiveX can cause Siebel 7 client software to lock up and become unusable.
The Siebel problem is one of several issues that prompted Microsoft to release a "compatibility patch" in conjunction with this month's security updates, which undoes the ActiveX changes for another 60 days.
Source:
http://www.computerworld.com/
News Story by Robert McMillan
APRIL 14, 2006 (COMPUTERWORLD) - Internet Explorer users are not the only people patching browsers this week.
The new version of the browser, Firefox 1.5.0.2, was released yesterday afternoon. It is being labeled a "stability and security" release by the Mozilla team, meaning that it addresses critical security problems as well as a number of other bugs.
Source:
http://www.computerworld.com/
News Story by Jeremy Kirk
APRIL 17, 2006 (IDG NEWS SERVICE) - Computers infected with a well-known piece of malware began downloading a new spam tool Sunday night used by hackers to send unwanted e-mail.
If a computer is infected with the
Bagle worm, a hacker can download other malicious programs to the machine. In turn, those programs can send out spam to other machines without the knowledge of the user.
Source:
http://www.computerworld.com/
News Story by Bob Brown
APRIL 14, 2006 (NETWORK WORLD) - When a new virus strikes, some of us might fall ill, some might die and others will survive. That's
the beauty of us each having a unique immune system.
"
One reason computers are so vulnerable to attack is that they are all the same," Forrest said. "In order for [buffer overflow and other attacks] to be introduced successfully, they require the attackers to know a lot about the program that the victim machine is running. The reason the attacker knows all of these details is because of widely replicated software."
Source:
http://www.computerworld.com/
BV MAHALAKSHMI
Posted online: Monday, April 17, 2006 at 0000 hours IST
... there were
misconceptions that biometrics is being used only in forensics. It has indeed moved far ahead and is now used to prevent unauthorised access to ATMs, cellular phones, smart cards, desktop PCs, workstations, and computer networks. What more, in automobiles, biometrics can replace keys with key-less entry devices!
...
According to Frost and Sullivan analysts,
non-automated fingerprint identification systems (Non-AFIS) is the prevalent biometric technology which is being adopted in the commercial sphere, in particular silicon swipe sensors. Moreover, leading silicon manufacturers have invested heavily in research and development of silicon swipe sensors to be used for both e-commerce and m-commerce.
Source:
http://www.financialexpress.com/
Q: Some computer experts are concerned about the security of electronic voting machines. What are some of the current safeguards in place to ensure vote accuracy?
A: Most of the objections raised by computer security experts do not take into account the total election process and the numerous security features built into the process as well as the equipment.
Hackers cannot hack into our system since it isn't connected to the Internet. The equipment cannot be re-programmed without physical access to the machines themselves, which is strictly limited. We test and retest the equipment.
Source:
http://www.jconline.com/
by Matthew Wade
Microsoft has made over 40 on-demand webcasts available for free - covering everything from computer security to guerilla marketing and financial management - following its recent Small Business Summit.
http://www.microsoft.com/smallbusiness/small-business-summit/hub.mspxSource:
http://www.itp.net/
April 15, 2006
Tom Espiner
ZDNet UK
April 13, 2006, 18:05 BST
The NASA hacker is currently fighting extradition to the US in what has been a protracted trial. He is charged with gaining unauthorised access to 97 US government computers, including machines belonging to NASA and the US Department of Defense. He claims he was searching for evidence of UFOs.
Source:
http://news.zdnet.co.uk/
"
There's no such thing as an unhackable network", says Robert Schifreen, author of "Defeating The Hacker" and the chairman of the hacking discussion panel. "By understanding what makes hackers tick", he continues, "you can increase the security of your systems by second-guessing them".
Source:
http://www.theitshield.com/
Automatic Patchwork - By Patrick Chisholm - Military Information TechnologyFaced with growing cyber attacks that target software security flaws, the Pentagon is mandating use of
automated patch-management technology designed to quickly protect networks against fast-moving threats.
There are as many as 20 flaws per 1,000 lines of software code, according to a Government Accountability Office (GAO) report, and hackers have become expert in exploiting the vulnerabilities that result.
Source:
http://www.military-information-technology.com/
April 12, 2006
Virus writers at war | Channel RegisterVXers are also turning against each other. Some cybercrims use malicious programs that destroy the software developed by rival groups. Malware authors are fighting each other for control of infected PCs. In early November 2005, for example, an attempt to hijack a botnet was detected that resulted in a network of infected computers changing hands three times in one day. "Criminals have realised that it is much simpler to obtain already infected resources than to maintain their own botnets, or to spend money on buying parts of botnets which are already in use," Kaspersky reports.
Source:
http://www.channelregister.co.uk/
Viruslist.com - Malware Evolution: 2005, part twoApr 03 2006
Yury Mashevsky
Virus Analyst, Kaspersky Lab
Milestones in 2005
Escalating confrontation
Increased response speed
That human factor again...
Other trends
New technologies
Rootkits
Business malware
Blackmail
User recommendations
Conclusion
Source:
http://www.viruslist.com/
Viruslist.com - Malware Evolution: 2005Feb 08 2006
Yury Mashevsky
Virus Analyst, Kaspersky Lab
This report provides statistical information and comment on significant events of the past year. It also examines the continuing growth in the market for malicious code, and includes an analysis of the current situation.
TrojWare — Trojan programs
VirWare — worms and viruses
MalWare — other malicious programs
Other trends
Internet banking
Malicious code for new platforms and multi-platform malicious code
AdWare
Conclusion
Source:
http://www.viruslist.com/
Cybercrime costs biz more than physical crime | Channel RegisterIBM said these procedures are a necessary first step but fail to go far enough. It advises organisations to
develop multi-layered defences in order to thwart hack attacks instead of taking a "patch or band-aid" approach to safeguarding corporations against information security attacks.
Source:
http://www.channelregister.co.uk/
MXI Security - Portable Security DevicesOutbacker MXP™ is a Portable Security Device. It is a completely portable USB powered, secure, multi-functional product with on-board processing for seamless, hardware based encryption, secure storage and strong authentication. Outbacker MXP provides unprecedented security, functionality and flexibility in the management of sensitive corporate information on a portable device as well as protection and assertion of personal and corporate digital identities.
Source:
http://www.mxisecurity.com/
Motorola Biometrics Solution Will Help Protect Delaware Citizens with Improved Identity TechnologyThe Motorola Printrak BIS is an integrated biometrics system that stores a variety of information including: fingerprints, palmprints, iris prints, facial images, signatures metrics, and descriptive information of the person fur use in areas such as job applications, e-passport and criminal investigation reports.
Source:
http://www.tmcnet.com/
Multi-State Information Sharing Analysis Center (ISAC)The goal is to have this MS-ISAC include all fifty states, which would provide a valuable centrally-coordinated mechanism for sharing important security intelligence and information between the States.
Source:
http://www.cscic.state.ny.us/
April 11, 2006
Wi-Fi Zeros In on Laptops'... - ComputerworldOpinion by Mark Hall
APRIL 10, 2006 (COMPUTERWORLD) - ...locations throughout much of the U.S. Fleet managers, security managers and the cartographically challenged get a new whereabouts weapon this week, when Skyhook Wireless Inc. in Boston releases a beta version of its Loki mapping service for mobile users.
Commercial users of Skyhook's Wi-Fi Positioning System software can track trucks equipped with laptops, say, and security managers can use the tool to track down missing machines.Source:
http://www.computerworld.com/
Kaspersky warns of cross-platform virus proof of concept - ComputerworldNews Story by Jaikumar Vijayan
APRIL 07, 2006 (COMPUTERWORLD) - Kaspersky Labs is reporting a new proof-of-concept virus capable of infecting both Windows and Linux systems.
The cross-platform virus is relatively simple and appears to have a low impact, according to Kaspersky. Even so, it could be a sign that virus writers are beginning to research ways of writing new code capable of infecting multiple platforms, said Shane Coursen, senior technical consultant at Kaspersky.
Source:
http://www.computerworld.com/
Securing Data When Data Is Everywhere - Computerworld...
We recently discovered that agency personnel often create Microsoft Access databases to help them manipulate data and create reports. The users who originate such databases, or the heads of their departments, may be deemed the owners of the data, but IT remains its custodian. Unfortunately, many data owners don't understand the concept of security controls, or even the need for them. It becomes the responsibility of IT security to implement the necessary controls.
...
Source:
http://www.computerworld.com/
Webcast SeriesThese pre-Tech·Ed 2006 webcasts enable IT professionals and developers to explore current and soon-to-be-released Microsoft technologies and evaluate a wide range of products and solutions for today’s IT environment.
Applying the Principle of Least Privilege to User Accounts on Windows XP...
The Least-Privileged User Account ApproachA
defense-in-depth strategy, with overlapping layers of security, is the best way to counter these threats, and the
least-privileged user account (LUA) approach is an important part of that defensive strategy. The LUA approach ensures that users follow the principle of least privilege and always log on with limited user accounts. This strategy also aims to limit the use of administrative credentials to administrators, and then only for administrative tasks.
...
Source:
http://www.microsoft.com/
Security Reference GuideYour hosts Cyrus Peikari and Seth Fogie
As a computer geek, family and friends often *let* me fix their computers. The first thing I notice is that most of them are all sharing the same account with their kids, neighbors, and sometimes the family dog.
Table of ContentsOverview
Web Application Security
Operating System Security
Network Security
Hardening Your System
Wireless Security new
Mobile Security
Data Forensics
Legal and Ethical Issues of Security
Home User Security new
Source:
http://www.informit.com/
Checklist: Top 10 best practices for securing e-mail clientsBy Richard Luckett
10 Aug 2005 | SearchExchange.com
Top 10 best practices for securing e-mail clients #1: Patch your clients
#2: Configure antivirus software to scan your e-mail clients
#3: Use anti-malware software
#4: Quarantine attachments
#5: Don't be a sucker
#6: Disable unsigned macros
#7: Use Outlook's Junk E-mail filter or install spam-filtering software
#8: Just be plain
#9: Learn to read (e-mail headers, that is)
#10: Digitally sign and encrypt e-mails
Source:
http://searchexchange.techtarget.com/
BY Michael Arnone
Published on Apr. 10, 2006
Pentium computers vulnerable to cyberattackVANCOUVER, British Columbia —The built-in procedure that Intel Pentium-powered computers use to blow off their digital steam could put users in hot water by making the machines vulnerable to cyberattacks, computer security researchers announced at the CanSecWest/core06 conference last week.
Source:
http://www.fcw.com/
Columbia Missourian - Man suing former employer for requiring his fingerprintsAlthough Attaway has declined to discuss his lawsuit, some members of his church, New Covenant Faith Center in Independence, believe that fingerprinting could be a “mark of the beast,” a symbol from the book of Revelation. Mentioned seven times, it warns Christians of the coming of the Antichrist. The 13th chapter of Revelation in particular prohibits God’s followers from being branded on their right hand or forehead. Some Christians have equated these marks with biometric fingerprinting and computer chip technology.
Source:
http://columbiamissourian.com/
Researcher: Web services security risks largely ignoredDuring a conference presentation, researcher Alex Stamos outlined how a number of Web services technologies, including the Asynchronous JavaScript + XML (AJAX ) and the XQuery query language could be exploited by hackers to dig up secret information and attack systems.
Source:
http://www.networkworld.com/
CIO IndiaMIT Assistant Professor Dina Katabi says incremental increases in wireless network throughput just aren't going to cut it. Her Colleague Rob Miller says phishing attacks continue to get trickier and more threatening, and that a "Web wallet" could be the answer to safer e-commerce. They are two of more than a dozen MIT faculty members presenting their latest research this week at the MIT Information Technology Conference.
Source:
http://www.cio.in/
ConsumerReports.org - Biometrics: Fingerprint scanners 4/06Log-in IDs, passwords, PIN codes, screen names, and online profiles. Does it seem like you have to remember way too much information to use your computer and log on to the Internet? There's a better way to manage computer and Internet access: Use a biometric security device such as a fingerprint scanner.
Source:
http://www.consumerreports.org/
April 09, 2006
Security Sales & IntegrationNo one has a real crystal ball to view the future, but it’s safe to say that biometrics for personal identification and authentication will one day find widespread use in the access control market, just as proximity did less than a decade ago. Biometrics is also likely to become one of the most controversial subjects of the 21st century.
Source:
http://www.securitysales.com/
Fadia’s advice: Develop a hacking attitudeAccording to him, network security is not only a concern for corporate and government institutions, but also affects the common people, many of those who become victims of unscrupulous and untraceable hackers while using various applications in the internet.
According to him,
the most dangerous kind of hacking are invasion of privacy, email forging and putting spyware on other systems to monitor their activities. He also warned the audience that one’s privacy is severely compromised if proper steps are not taken to protect it. ‘‘Internet Protocol address of each computer is unique and one should protect it. While using email, chatting, clicking on web related features, the information in one’s computer is easily made accessible to others.’’ he said.
Source:
http://cities.expressindia.com/
April 08, 2006
Ericka Chickowski
6 Apr 2006 21:51
Researchers from Harvard University and the University of California at Berkeley released a paper last week on why users fall for phishing scams, concluding that current anti-phishing deterrents are ineffective.
...
A different approach is needed in the design of website security systems, the researchers concluded.
...
"Rather than approaching the problem solely from a traditional cryptography-based security framework,
a usable design must take into account what humans do well and what they do not do well," they wrote.
Source:
http://www.scmagazine.com/
April 06, 2006
Simon Hayes and James Riley
APRIL 04, 2006
The deal builds on Microsoft's 2003 agreement to allow the government to examine source code for Windows and Office.
...
That agreement followed an increase in the popularity of open source software.
...
Microsoft opened its code to select governments to prove its technology was as safe as any other, but not all governments were happy with the access restrictions imposed by Microsoft.
...
China, Russia, Britain and NATO signatory countries are among other nations to have signed that agreement.
...
Source:
http://australianit.news.com.au/
BY PETE BARLAS
INVESTOR'S BUSINESS DAILY
Posted 4/5/2006
"The whole thing to understanding a hacker is learning about the hackers' tools and techniques and how to use those things against them," he said.
Source:
http://www.investors.com/
By Eric Benderoff
Tribune staff reporter
Published April 4, 2006, 10:05 PM CDT
Computer security experts were pleased Tuesday that New York Atty. Gen. Eliot Spitzer filed a new lawsuit in the battle to stop Internet companies from illegally installing unwanted and "deceptive" software on computers.
Source:
http://www.chicagotribune.com/
April 04, 2006
Sony, Apple and especially Microsoft illustrate differing approaches to Digital Rights Management.
By Simson Garfinkel
Rootkits and iPodsDRM got a bad name this past Christmas season when Sony, now a major record label, snuck a DRM technology (involving a rootkit) onto several dozen musical discs that it was selling.
The discs played just fine in a conventional CD player, but put one into a PC running the Windows operating system and the CD would covertly install a program that was designed to limit what the consumer could do with the disc that he had just purchased. Unfortunately, the Sony software also damaged the PC, rendering the computers vulnerable to attack by hackers and, in some cases, making the computer crash. Sony suffered a huge amount of embarrassment from the incident, was targeted by several class-action lawsuits and was ultimately forced to recall millions of discs.
Source:
http://www.csoonline.com/
INDIATIMES NEWS NETWORK[ TUESDAY, APRIL 04, 2006 08:20:04 PM]
Advances in technology has pushed a plethora of new hi-tech options- from biometric to voice controlled and keystroke or password controlled access - for the HR-minded. Read on ....

Once the stuff of futuristics and science fiction, Electronic Access Control and Biometrics — the authentication of identities through unique physical or behavioural traits of individuals — is fast emerging.
Source:
http://economictimes.indiatimes.com/
April 03, 2006
Just the other day a friend asked me which was better: WEP (Wired Equivalent Privacy) or WPA (Wi-Fi Protected Access) for wireless security at home . If you have ever attempted to connect to a wi-fi hotspot and you had to enter a password to connect, it most likely has one of these security modes turned on. It's a good idea to have one of these modes enabled on your router at home if you have one too. Otherwise you are providing your neighbors with free internet access and opening your home network up to unscrupulous attacks. I recently found the Wi-Fi Alliance website and it has some great info, though more technical than most will enjoy.
Source:
http://www.theronhatch.com/
APRIL 3, 2006
Computer Security
By Brian Grow
"Lawsuit against you," reads the subject line in an e-mail that hit thousands of in-boxes around the world last month. In flawless legalese, the message warns recipients that they recently sent an unsolicited fax to the sender's office. Citing U.S. civil code, its prohibition on sending junk faxes, and an actual $11 million settlement by restaurant chain Hooters, the missive threatens a lawsuit over the alleged junk fax.
In today's litigious -- and digital -- society, being notified of a lawsuit via e-mail might not seem too unusual, right? Gotcha! The e-mail is a scam that preys on deep-seated fears of being hauled into court. Its target: unlucky recipients who may indeed be among thousands of companies that send junk faxes.
Source:
http://www.businessweek.com/
Hackers have raised the stakes with a new bug almost immune to detection As a data security specialist, Jeremy Pickett sees all kinds of digital tricks. So on Mar. 20, when he was tracing the origins of a computer bug that had been blocked the night before from entering a client's computer network, Pickett wasn't too surprised that it tried to connect with four sleazy Web sites, most of them, he believes, in Russia. Or that it then tried to load victims' PCs with as many as 30 new pieces of "malware," ranging from spam programs to those that automatically dial in to expensive phone-sex services.
But the real shock came when Pickett decided to test another bug by infecting his own PC with it. Out slithered a program that promptly installed itself deep inside his computer. There it became virtually immune to detection from the basic antivirus software that scans for dangerous code. The bug -- known as a "Trojan," which in turn was hidden inside a "rootkit" -- was designed to activate whenever a Web surfer typed in a user name or password for bank accounts or Web sites for dating, social networking, or e-mail. Pickett went to a bank site and entered fictitious log-in information. Right before his eyes, those data were sent streaming back to Russia, joining the IDs of thousands of real victims. His reaction: "absolute horror."
Source:
http://www.businessweek.com/
LUND, SWEDEN -- (MARKET WIRE) -- 04/03/2006 -- Precise Biometrics AB (publ), a Swedish company that develops and sells world-leading and user-friendly biometric security solutions based on fingerprints and smart cards, has received a follow-up order from the Thai authorities concerning biometrics for national ID cards. Precise Biometrics estimates that the expected revenue during a three-year period will generate about SEK 20 million. The Thailand project in its entirety means that Precise Biometrics, together with Smart Card Systems International Co, Ltd (SSI), will be delivering biometrics for the national ID card to all of Thailand's 64 million citizens.
Source:
http://www.marketwire.com/
Monday April 3, 6:00 am ET
Certicom Security for Sensor Networks enables networks to be scalable, mobile and self-configurable
MISSISSAUGA, ON, April 3 /PRNewswire-FirstCall/ - Certicom Corp. (TSX: CIC - News) today launched Certicom Security for Sensor Networks, a software module and hardware IP core, that secures low-power, wireless sensor networks. The products use elliptic- curve cryptography (ECC) to add a provable identity to sensor devices, which provides security and reliability from design and development through to the manufacturing, deployment and upgrade of a sensor network.
Today's wireless sensor networks are generally small (fewer than 100 nodes) so symmetric cryptography with centralized control of security is sufficient. However, for sensor networks to reach their potential - to build large, self-healing networks that allow nodes to move as necessary - developers of microcontrollers and sensor networking stacks must move to public-key cryptography, which enables devices to interact and communicate securely. ECC provides more security per bit than other public-key cryptography schemes making it the only option that can meet the footprint and power limitations of a sensor network's constrained devices.
Source:
http://biz.yahoo.com/
Sam Vaknin, Ph.D. - 4/4/2006
An Epistolary Dialogue Between Roberto Calvo Macias and Sam Vaknin, author of "Malignant Self Love - Narcissism Revisited".
Here is a quote I found somewhere, I don't even recall where:
"Only art history still knows that the famed geniuses of the Renaissance did not just create paintings and buildings, but calculated fortresses and constructed war machines. If the phantasm of all Information Warfare, to reduce war to software and its forms of death to operating system crashes, were to come true, lonesome hackers would take the place of the historic artist-engineers."
This is a problematic statement because it ignores the emergent property of genius. The "famed geniuses of the Renaissance" did not interact with their calf hide and sharpened quills the same way an hacker interacts with the network or even with his computer. Hackers are, by definition, dependent on computing collectives. Galileo worked in the solitude of his rooms during his long inquisition-imposed house arrest. An hacker without vast and sprawling communications and computing (information) networks is dead, paralysed, a non-entity. Paradoxically, the hacker is by far the most social artist ever to have existed. The romantic view of the hacker (lonely, tortured genius, a-la Van Gogh) is the result of ignorance and fear. Genius today is a distributed, collective phenomenon and the medium of the hacker is the distributed, collective network. The internet is a mass phenomenon, a MOB phenomenon, in the derogatory sense that Jose Ortega y Gassett used - but it is also a chance to focus the actions of millions of individuals into a coherent, powerful, laser beam of awareness and activism.
Source:
http://globalpolitician.com/
By Seth Fogie.
Date: Mar 31, 2006.
Imagine if you just graduated with an IS degree and landed a job at a small business as their only IT staffer. You know your way around an operating system and understand some of the protocols and programs that keep data flowing, but for the most part your skills are untested in the real world. Regardless, you are the only thing separating the company's users and data from downtime. Sound like a tough situation? Oh, I forgot to mention there are four of the best hackers in the world trying to get into your digital domain and steal anything of value, including a database of 10,000 credit card numbers. This isn't something seasoned administrators would want to face, much less fresh graduates.
Source:
http://www.informit.com/
April 02, 2006
By Fernando Cassia in Argentina: Friday 31 March 2006, 21:30
A GROUP of Argentinean students and graduates has compatible Java VM code and has contributed it to the Apache Software Foundation's project to create an open source, J2SE 5.0-compatible java runtime and virtual machine. The project has received Sun's blessing, with Graham Hamilton from Sun commenting in his blog: "The licensing rules for J2SE 5.0 were carefully designed to allow independent, compatible open-source implementations of the J2SE specification".
Source:
http://www.theinquirer.net/
As Valley goes high tech, security becomes an important issue
By David Royer/staff
droyer@newsleader.com
Piggybacking, using someone else's wireless connection without their knowledge, is a legal "gray area," computer experts say. Legal or not, leaving wireless Internet connections open without proper security is like walking out of the house without closing the door.
Source:
http://www.newsleader.com/
April 01, 2006
By Larry Greenemeier
Courtesy of InformationWeek
Advances in standards and technology have Visa believing now's the time for the United States to embrace radio-frequency-enabled contactless payment devices that can be waved near a sensor rather than having to be swiped through a card reader. These devices can take the form of a standard credit or debit card, a chip implanted in a cell phone, or a mini card that's about half the size of a conventional credit card.
Source:
http://www.securitypipeline.com/
By Antone Gonsalves
Courtesy of TechWeb News
The hackers entered two servers running Microsoft Internet Information Services and planted the script needed to redirect people from the banks' legitimate sites to a bogus one, Quarterman said in
his blog.
"
This new scam is like phishing without the intervening electronic mail step," Quarterman said. "Because it is the bank's own Web (hosted, in this and no doubt many other cases) server that is compromised, the customer has even less reason to suspect anything amiss."
Source:
http://www.securitypipeline.com/
By Antone Gonsalves
Courtesy of TechWeb News
The patented technology enables a browser to call programs over the Internet to display streaming audio and video, advanced graphics and other content within a single Web page. The technology has become a standard within the language used to write Web pages, called Hypertext Markup Language.
The modification planned by Microsoft would change the way the browser handles ActiveX controls related to rich content. As a result, a person would have to manually activate a stream either by clicking on it or using the "tab" and "enter" keys on a keyboard, the company said in its
security blog.
Source:
http://www.securitypipeline.com/


